Create Your Own SSH UDP REQUEST Account
Secure and Easy Tunneling with Free Premium UDP REQUEST Account – Active for 7 or 5 Days
SSH UDP REQUEST Server in USA
Please don’t use Torrent, DDoS, Spamming and any illegal activity with our server!
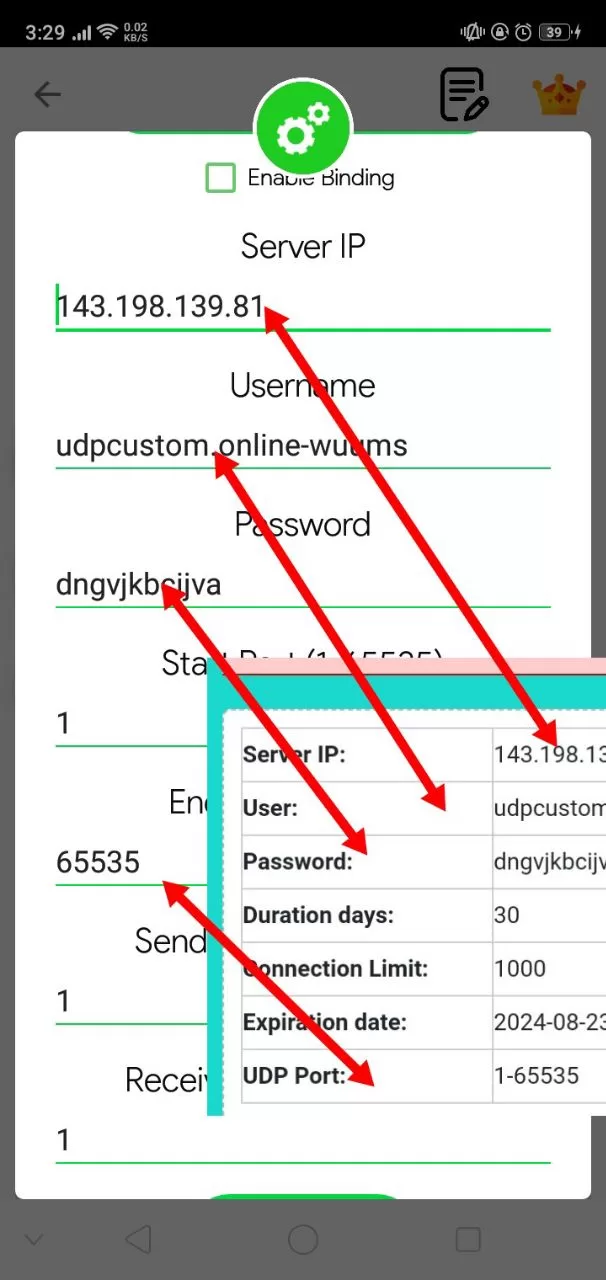
UDP Server Creation
How to Use Socks IP
UDP and SSH Tunneling: An Overview
Introduction
In the world of networking and cybersecurity, UDP (User Datagram Protocol) and SSH (Secure Shell) tunneling are two important concepts that play crucial roles in data transmission and secure remote access. This article will explore these technologies, their uses, and how they can be combined to enhance network security and functionality.
UDP (User Datagram Protocol)
What is UDP?
UDP is a connectionless transport layer protocol that is part of the Internet Protocol suite. It provides a simple, unreliable method for sending data packets (called datagrams) over a network.
Key characteristics of UDP:
- Connectionless: UDP doesn’t establish a connection before sending data.
- Unreliable: There’s no guarantee that packets will arrive in order or at all.
- Low overhead: UDP has minimal protocol overhead, making it faster than TCP.
- No congestion control: UDP doesn’t slow down when the network is congested.
Common uses of UDP:
- Real-time applications (VoIP, online gaming)
- DNS (Domain Name System) queries
- Streaming media
- DHCP (Dynamic Host Configuration Protocol)
SSH (Secure Shell) Tunneling
What is SSH Tunneling?
SSH tunneling, also known as SSH port forwarding, is a method of transporting arbitrary data over an encrypted SSH connection. It can be used to add encryption to legacy applications, implement VPNs (Virtual Private Networks), and bypass firewalls.
Types of SSH Tunnels:
- Local Port Forwarding
- Remote Port Forwarding
- Dynamic Port Forwarding (SOCKS proxy)
Benefits of SSH Tunneling:
- Encrypted data transfer
- Bypass firewalls and network restrictions
- Secure access to services on remote networks
- Hide the true origin of network connections
Combining UDP and SSH Tunneling
While SSH typically uses TCP (Transmission Control Protocol) for its connections, it is possible to tunnel UDP traffic through an SSH connection. This can be useful in scenarios where you need the benefits of both UDP and SSH.
Use cases for UDP over SSH:
- Securing real-time applications that use UDP
- Bypassing firewalls that block UDP traffic
- Encrypting DNS queries
- Improving the security of online gaming or VoIP applications
Implementation Challenges:
- Additional overhead due to encapsulation
- Potential increase in latency
- Complexity in setup and configuration
Conclusion
UDP and SSH tunneling are powerful networking tools that, when used appropriately, can significantly enhance the security and functionality of network communications. By understanding these technologies and their potential combinations, network administrators and security professionals can design more robust and flexible network architectures.
As with any advanced networking technique, it’s crucial to consider the specific requirements of your application, the network environment, and potential security implications when implementing UDP over SSH tunneling or similar solutions.
